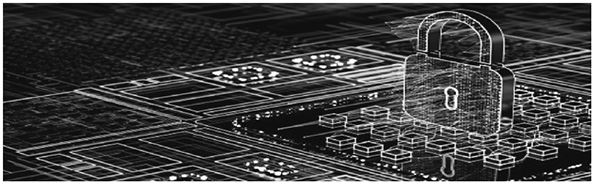
People are using various electronic devices and the Internet to the point where the saying applies that, “People cannot live without the Internet.” They sign up for online classes, contact friends on social media, and remotely control home appliances on their smartphones. In addition, various tasks and services are all processed through the computer network. It is convenient because everything is connected through the Internet. However, if even a small problem occurs in the cyber universe, society will be paralyzed and people will be petrified. Moreover, criminal acts such as leaking personal information resulting in exploitation and bribery are also increasing. However, many people are insensitive to personal information leakage or hacking because cyberspace is abstract and invisible. In a world that relies on the Internet, is it okay to be indifferent to these things? What seriousness do these issues have that makes them so important?
[Information Related Damage Cases]
On Sept. 3, the YouTube channel “Korea Government” run by the Ministry of Culture, Sports, and Tourism was hacked for about four hours. The channel name was changed by the hacker, and a video related to cryptocurrency, totally unrelated to the channel, was posted. On the same day, the Korea Tourism Organization’s overseas promotional YouTube channel “Imagine Your Korea” was also hacked for nefarious purposes.
At a high school in Gwangju, the final exam papers for the first semester of the second grade were leaked. According to the investigation, two students sneaked into the staffroom and installed a malignant code on the computers to leak test papers and answer sheets. The code was programmed to automatically take and store screenshots at regular intervals.
In addition, news related to cyberspatial crimes has recently been frequently reported, such as hacking of celebrities’ social media accounts resulting in the leaking of private photos. Various companies and institutions have also been the target of hackers who then leaked private information.
[Information Protection and Security, Hacking and Cracking]
“Information protection” and “Information security” are often used interchangeably in virtually the same terms because there are no clear criteria for distinguishing the meaning. Therefore, the reality is that both expressions are considered correct no matter when they are used. However, according to the standards of the Korea Institute of Information Security & Cryptology (KIISC), information protection is a comprehensive act of protecting information, and information security is the specific management and technology that focuses on confidentiality.
The opposite concepts are hacking and cracking. In fact, these words were not used in a negative way from the beginning. According to the Korea Internet & Security Agency (KISA), hackers are “people who are absorbed in the internal structure and operation of computer systems and strive to know them, most of whom have excellent computer and communication skills.” What hackers do is called hacking, but as the meaning gradually changed over time. Hacking is now often used to mean “illegally accessing the weak security network of a computer network or having a harmful effect on an information system.” Cracking is the act of destroying other people’s computer systems or communication networks through illegal access such as hacking. Therefore, hackers who commit criminal acts are defined as “crackers,” but in reality, hackers and crackers are used without distinction. Recently, it is divided into “white hackers” who use hacking for defense and security, and “black hackers” who use it for information leakage and criminal activities.

[Importance of Protecting Information, and Danger of Hacking]
Then, why is information protection important? CBT reporters interviewed information security professional Shin Dong-hwi of STEALIEN Inc. CTO, a cybersecurity incorporation about this. He said, “In the past, an individual existed in a physical space, and its existence was clear. However, now there is another object in the Internet world that is identified with a physical individual. Moreover, as IT has evolved from the past to the present, the location of data is shifting from paper to the IT environment, and a significant number of data is now in it. In the past, physical identification cards were presented to prove identity, and so it was important for the individual to manage them well. Today, there are many ways to identify yourself in your IT environment. Therefore, managing and protecting the tools you need to use, such as account information, is as important as having to manage your identification in the past. Now, if you cannot protect your information, you can disadvantage yourself in the IT environment. In severe cases, you may fall victim to crimes such as voice phishing, or you may lose your competitiveness due to personal information leakage or corporate confidentiality leakage. Therefore, information protection is important for both individuals, businesses, and countries.” As much as modern society relies on the Internet, information becomes a personal property. If such information is attacked by hacking, there is a risk of significant loss, both personally and nationally.
On the contrary, hacking is very dangerous because it is often difficult to even know the occurrence of hacking damage. Cyberspace has no boundaries, so hacking is taking place 24 hours a day in infinite space. It is often possible to recognize that hacking occurred only when unauthorized access records are discovered, because it cannot be checked in real time all the time. In addition, in recent years, various services such as e-mail, payment, and games are often integrated and used with one Internet account, which may cause more damage due to hacking.
[The Most Frequent Hacking Attacks and Countermeasures]
When it comes to “hacking,” it is rather cliche and vague. The CBT reporters asked CTO Shin Dong-hwi about the frequent hacking damage and countermeasures.
Q1. The CBT reporters know that there are many techniques for hacking. Among them, what are the most frequently used, and what is the most common damage to the ordinary citizen?
The representative attacks that occur frequently to the ordinary citizen are “phishing,” and specifically voice phishing and smishing (SMS + phishing). In addition, there are ransomware (ransom + software) that both individuals and businesses are recently concerned about, and there are countless cases. There is also hacking of accounts such as social media, but this needs to be considered in detail. Social media account hacking is a problem with the social media service, and direct hacking of the account rarely occurs. In most cases, it is common for attackers to collect information from relatively low-security services and apply the collected information to social media. The reason for this attack is users using the same and vulnerable passwords for multiple services.
Q2. Then, after falling victim to cybercrimes like phishing, what is the best course of action?
Depending on the situation there are different solutions on the table. In the whole phishing scenario, there is a high probability of no real damage if victims noticed the hacking damage earlier. In this situation, victims can inform the real owner whose account is used to deceive others of the situation. They can also identify what personal information the attacker knows about them, and respond by updating services’ account information which is expected to contain some personal information. However, if the situation is serious it will be prudent to request banks to immediately suspend all transactions and report the situation to the police. Also, it is best to update separate services’ account information as I mentioned earlier.
[Efforts to Prevent Damage Caused by Hacking]
It is important how readers respond when damages are caused by hacking, but eventually the most important thing is to prevent hacking damage in advance. What can ordinary citizens do to prevent hacking damage? CTO Shin Dong-hwi had the following to say about this.
“There are many things to do to prevent damage caused by hacking in different conditions, the most important is efforts to protect your account. Here are some of the things you need to do to manage your account.
- To set up different passwords for each service. Passwords should be difficult including the following: Number + Small Letter + Capital Letter + Special Symbol.
- To change passwords regularly.
- To utilize the active means of verification which each service provides: SMS verification, Google OTP (One Time Password), etc.
- To minimize the unnecessary approaching and joining of services.
Also, I strongly recommend updating the devices you use. The “devices you use” are not only the obvious things like mobile phones, desktop computers, or laptops but also TVs, routers, webcams and security cameras which people use in their homes. We can reduce the likelihood of hacking when users pay attention to the products they use, notice the contents that have problems, and immediately run the updates that manufacturers provide.”
Additionally there is the “Korean ID Checker,” service which can check if there is a history of leakage from sites such as the “Dark Web” where frequently used IDs and passwords are available on the black market. This service can identify and delete doubtful accounts suspected of identity theft, and eliminates unnecessary websites.
The world cannot go round without the Internet. The more time goes by, the higher the importance of information protection becomes. It is time for readers, who use the Internet every day, to take personal responsibility to protect information.
By Seok Yeon-ji | duswl1102@chungbuk.ac.kr
By Kim Ye-rin | ering0325@chungbuk.ac.kr

 All
All Feature
Feature






 Seok Yeon-ji&Kim Ye-rin
Seok Yeon-ji&Kim Ye-rin